Secure Server Access in an Era of Network Isolation: Multi-hop Bidirectional Tunneling via the SSH Protocol

Overview
In today’s diverse business environments, organizations are actively employing various methods to restrict access routes in order to protect critical assets. Security solutions such as firewalls, access control lists (ACLs), and proxy servers play a crucial role in blocking unauthorized external access. These security measures have become essential in defending against increasingly sophisticated cyber threats.
Beyond basic network segmentation, many companies are now building multi-layered network environments with progressively segmented stages to further safeguard internal resources. While this strategy enhances security, it also increases the complexity of legitimate access paths. Tunneling technology based on the SSH (Secure Shell) protocol provides a powerful solution for establishing secure and efficient communication channels, even within such complex network architectures.
Problem Statement and Underlying Technologies
Access Challenges in Isolated Network Environments
Accessing internal servers within isolated network environments is often complex and cumbersome. Typically, users must traverse multiple Bastion Hosts (also known as Jump Servers), requiring them to know the connection details—such as IP addresses, ports, and authentication credentials—for each intermediary server. Additionally, users must authenticate at every step, resulting in a multi-stage connection process that significantly hampers operational efficiency and negatively impacts the user experience.
Capabilities and Limitations of the SSH Protocol
SSH offers robust encryption and authentication mechanisms, making it a widely adopted solution for secure remote server management and file transfers. Its port forwarding (tunneling) capabilities are especially valuable in environments with stringent network restrictions.
The SSH protocol partially addresses multi-hop access through its JumpHost functionality. By using the ssh -J option, users can connect to a target server via one or more intermediary hosts in a single command. However, this approach still presents challenges: users must have knowledge of the intermediary hosts’ credentials, which may conflict with internal security policies. Moreover, if this access information is exposed, it could be exploited by malicious actors, posing a significant security risk.
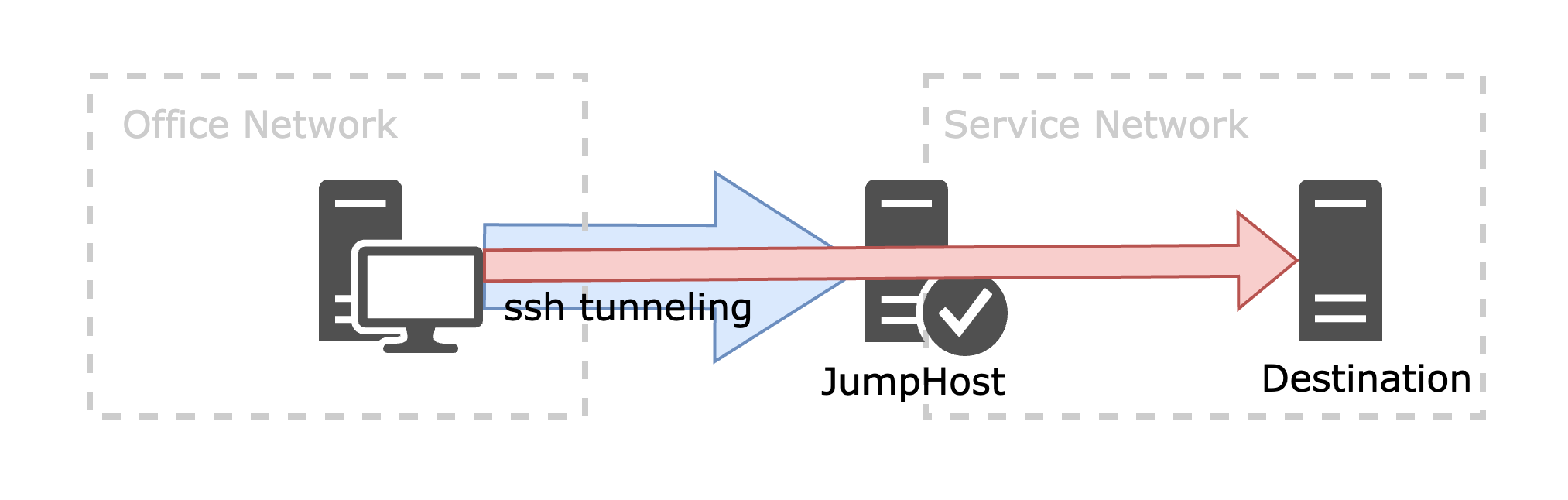
Inbound Access Restrictions and Reverse Tunneling
As security demands grow stricter, many organizations are implementing policies that completely block inbound access to their internal networks. In such environments, traditional SSH connections and JumpHost methods become ineffective for accessing internal resources.
This is where Reverse Tunneling emerges as a practical solution. Reverse tunneling works by establishing a connection from the internal network to an external relay server, effectively enabling access to internal systems from the outside through that pre-established channel. Specifically, a server within the internal network initiates an SSH connection to an external reverse tunneling server. Once the tunnel is established, external users can securely connect to the internal server via the relay.
This method enables secure access to internal resources even when inbound traffic is fully restricted, ensuring compliance with strict security policies while maintaining essential accessibility.
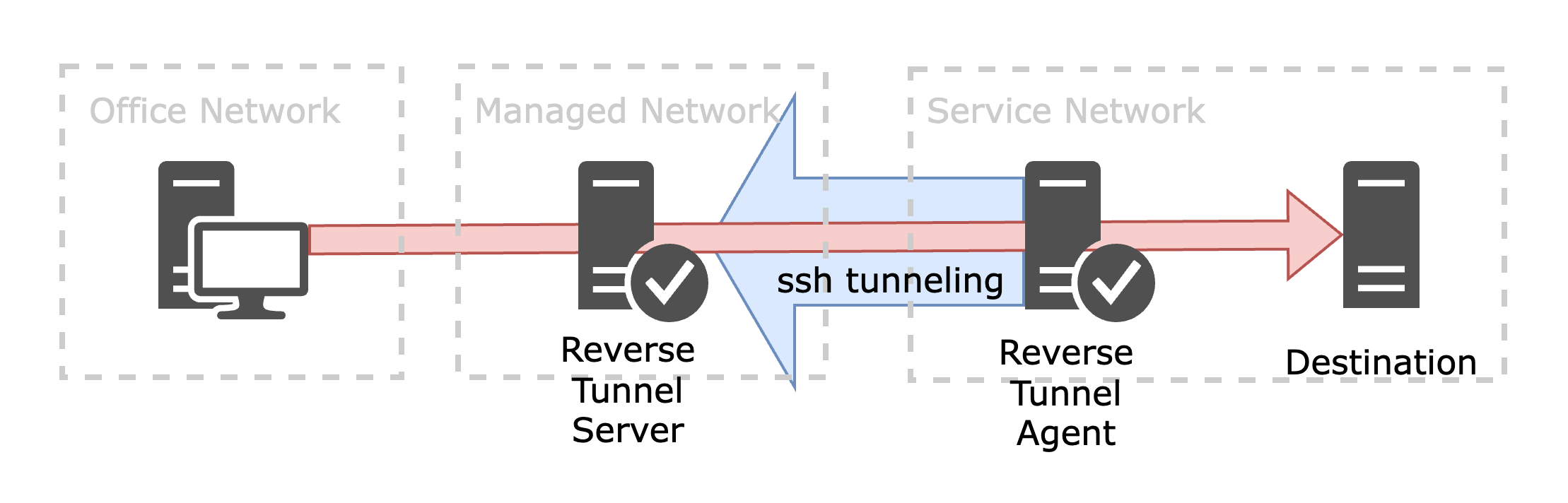
Complexities in User Access Control
Although SSH-based JumpHost and reverse tunneling methods are technically viable, managing granular user access becomes increasingly challenging in large-scale environments. When multiple users require selective access to various internal servers, maintaining SSH keys and configuring access control policies can quickly grow complex and error-prone.
Moreover, routine tasks such as user account management, permission updates, and audit logging are often performed manually, leading to substantial administrative overhead and increasing the risk of misconfiguration or security gaps.
The Need for Alternative Technologies and Integrated Solutions
To overcome these challenges, agent-based access control solutions have gained traction. Open-source tools such as Teleport streamline SSH access while providing robust access control and auditing features. However, even these tools may require additional setup in multi-hop environments or networks with specialized architectures.
As a result, modern isolated network environments demand an integrated solution that meets the following criteria:
- Users should be able to connect to target servers without needing to know the connection details of intermediary systems.
- The solution must provide secure user authentication and fine-grained access control.
- Internal resources must remain accessible even when inbound traffic is fully blocked.
- Administrators should have the ability to centrally monitor and audit all access activities.
- High security standards must be met without compromising usability or operational efficiency.
QueryPie’s Solution
Simplified Access to Layered Networks
QueryPie delivers a seamless and intuitive access experience, even in complex, multi-layered network environments. Users establish a single SSH connection to QueryPie, through which they can securely access the required internal servers—regardless of the underlying network structure. This approach significantly enhances user experience while also strengthening security by eliminating the need to expose connection details of intermediary servers.
Centralized Access Control
A core strength of QueryPie is its centralized control over network paths and user permissions. Administrators can configure and manage access policies directly through the QueryPie management console, specifying which servers each user is allowed to access and determining the optimal connection routes—whether through JumpHosts, reverse tunnels, or other pathways. These configurations are handled entirely by administrators, relieving end users of any need to understand or manage complex access routes. Users simply click to connect to the servers they’re authorized to access, ensuring both operational simplicity and strong security enforcement.
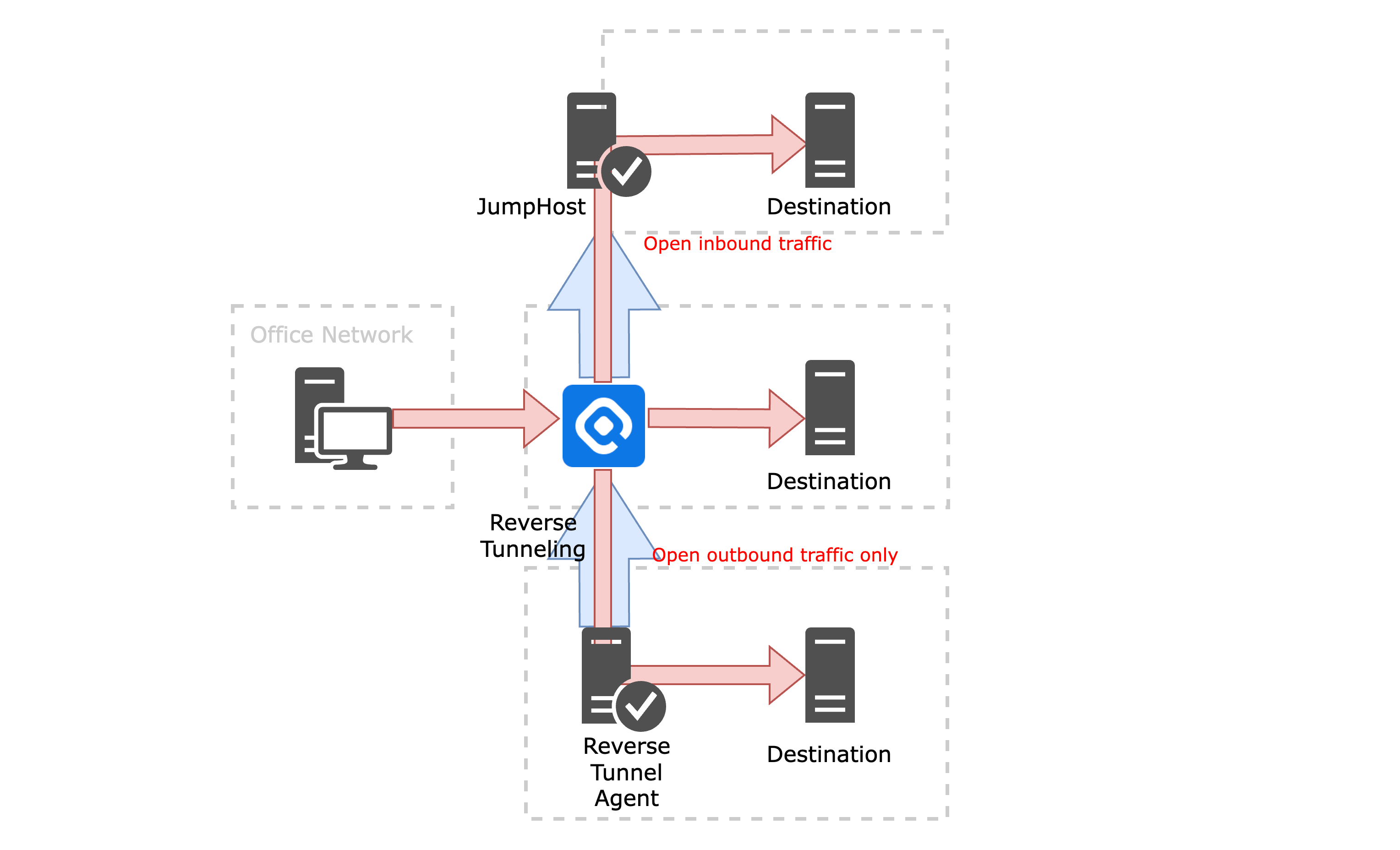
Flexible JumpHost Support
QueryPie enables multi-hop access through support for the traditional SSH JumpHost mechanism. Administrators can designate intermediary servers that users pass through to reach their final destination. These JumpHost servers are typically used exclusively for tunneling, and direct shell access to them is discouraged in favor of adhering to the principle of least privilege—thereby reducing the potential attack surface.
While the JumpHost method is relatively straightforward to configure, it introduces a security consideration: connection details of the intermediate servers must be stored within the QueryPie system. To accommodate environments with stricter security requirements, QueryPie also offers robust support for Reverse Tunneling.
Support for Reverse Tunneling
QueryPie’s reverse tunneling capability is built on the standard SSH reverse tunneling protocol. SSH was selected for its proven reliability, strong security, and ability to support fine-grained, connection-specific tunnels.
In this model, a server within the internal network initiates an outbound SSH connection to the QueryPie server. External users can then securely access the internal server through this pre-established tunnel. Unlike the JumpHost method, this approach requires no inbound connectivity to the internal network, allowing organizations to maintain strict firewall policies without sacrificing secure access.
Recognizing that reverse tunneling scenarios may also involve multiple network hops, QueryPie is actively developing support for multi-hop reverse tunnels to meet the needs of more complex architectures.
Innovative Tag-Based Routing
One of QueryPie’s standout features is its tag-based routing system, designed to simplify access management in dynamic infrastructure environments. Traditional configurations often require manual setup or static grouping of servers—an approach that becomes increasingly inefficient in modern cloud environments, where servers are frequently created, scaled, or terminated.
QueryPie addresses this challenge with a flexible tagging mechanism. Administrators can assign tags to servers and define access policies based on these tags. For instance, all servers labeled “production” can be automatically routed through a designated JumpHost or Reverse Tunnel, without the need for manual reconfiguration.
This tag-based approach is particularly valuable for managing auto-scaling infrastructure in cloud-native environments, where agility, automation, and scalability are essential.
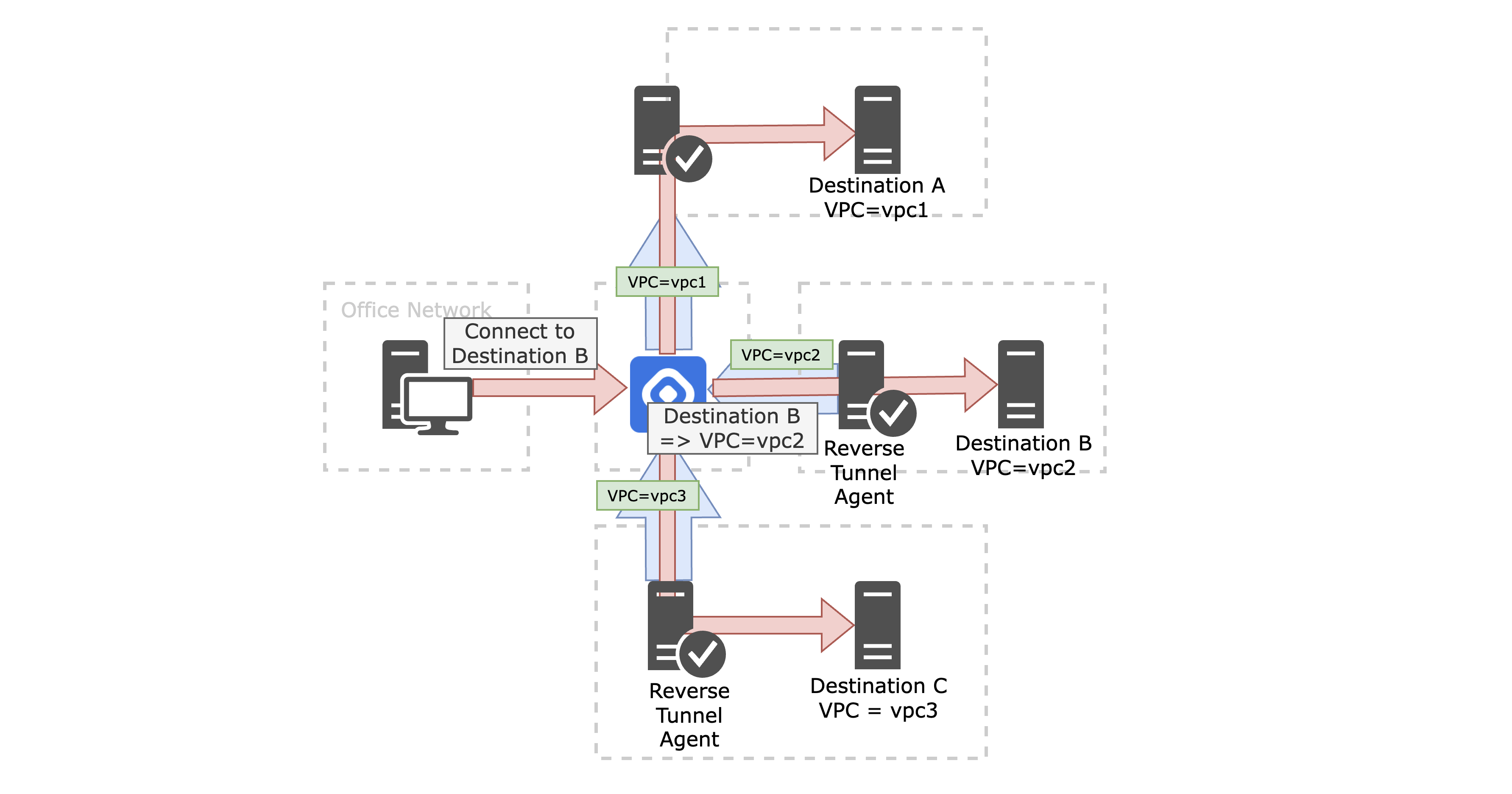
Real-World Use Case: Resolving IP Conflicts in Multi-Cloud Environments
QueryPie’s tag-based routing system is designed to tackle a wide range of complex network challenges. A notable example involves resolving IP address conflicts for customers operating across multiple AWS accounts. In multi-cloud or multi-account environments, it's common for different AWS accounts or VPCs to use overlapping private IP ranges—making traditional IP-based routing unreliable or ineffective.
QueryPie addresses this issue by combining tag-based routing combined with Reverse Tunneling. Each server is tagged to reflect its associated account or environment, and QueryPie intelligently uses this metadata to determine the appropriate Reverse Tunnel path. As a result, users can connect to the intended server using intuitive tags or server names, without needing to manage or even be aware of conflicting IP addresses.
Conclusion
QueryPie offers a forward-thinking solution that balances robust security with a seamless user experience, even in complex, multi-layered network environments. By enabling secure access to target servers without revealing the details of intermediate systems, QueryPie simplifies network traversal while upholding stringent security standards.
Supporting both JumpHost and Reverse Tunneling methods, QueryPie provides the flexibility organizations need to align with their specific network architectures and security policies. With full support for multi-hop configurations, the platform is well-suited to adapt to even the most intricate environments.
Through its comprehensive access capabilities, QueryPie empowers modern enterprises to meet evolving operational and security demands—without compromising efficiency or control.
Curious?
Reveal the Magic!
Please fill out the form to unlock your exclusive content!
