The Overlooked Command Bypass Issue: Let’s Finally Talk About It!
November 22, 2024
The Blind Spot of Command Bypass in Server Access Control
Having worked in IT security and information protection in enterprises, I've often encountered a situation where server access control solutions are implemented to block dangerous commands like sudo and rm -rf in an effort to prevent attacks leveraging security vulnerabilities.
However, despite these controls, many users manage to bypass the restrictions and execute the blocked commands. Even when controls are clearly set, some users will still find ways to breach the system security and run prohibited commands.
One common method to bypass these controls is through the use of shell scripts.
For example, on a test server, you might upload a shell script containing prohibited commands and then attempt to execute it after accessing the server with server access controls in place. You would then check to see if the execution is blocked.
Moreover, in many cases, the approved work plan may list only certain commands or scripts, but the actual contents of the script may not be transparent. In some instances, administrators may configure batch files or cron jobs to execute specific scripts periodically, changing the content of the scripts as a way to bypass both the work plan and the server access control configurations. Security professionals may have discovered these practices while performing infrastructure management audits.
Therefore, a common question posed by security professionals after meetings about server access control with enterprise-level tech security teams is:
“How do we block command bypass execution through shell scripts?”
"..."
Today, I’ll open the Pandora’s box of server privileged access management—an area that server auditors and security practitioners often try to avoid confronting.
The Importance of Server Access Control Solutions to Prevent Command Bypass Execution
To block command bypass execution, the key is using a server access control solution that supports this functionality. Such a solution helps manage command bypass attempts and prevents the execution of unauthorized commands.
QueryPie is one of the leading solutions that effectively blocks command bypass execution. Here's how it works:
- When a user accesses a server via the QueryPie Gateway and attempts to execute a command,
- The actual command (including the content of any scripts) is sent back to the QueryPie server for verification,
- It is checked against a predefined list of blocked commands.
By using this approach, QueryPie can prevent the execution of bypass commands before they are executed, based on the pre-defined blocklist, even if the user is connected to the server.
One key benefit of this approach is that there's no need to install additional agents on each server. Through centralized management, security policies can be applied consistently across all servers. This means security policies can be quickly deployed without additional software installations or complex deployment processes.
Of course, there are some technical limitations to this approach. For example:
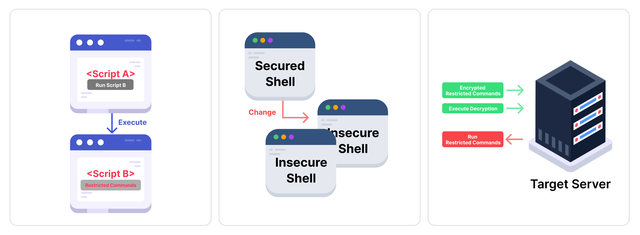
- Scripts calling other scripts that contain blocked commands,
- Attempting to bypass the shell using a different shell,
- Using Base64 encoding to decode commands on the server side.
To address these issues, QueryPie has designed mechanisms to block commands when another script is called within a script, as well as prevent shell command execution or decoding/encryption commands. This ensures that security measures remain effective even in these scenarios.
Next-Generation Command Blocking Features: Enhancing QueryPie's Security and Usability
QueryPie continues to improve both security and usability, and it is constantly evolving to provide higher levels of security with its command blocking features. While it currently supports only Bash Shell, QueryPie plans to gradually support other shells, including Zsh, to better align with customers' environments. This flexibility will allow users to choose the shell that suits their setup and create a more secure server environment.
Additionally, QueryPie has developed the technical capabilities to block command bypasses, even when a script calls other scripts multiple times. This innovation offers a unique command-blocking solution that isn't available in many other security systems, significantly strengthening the overall security.
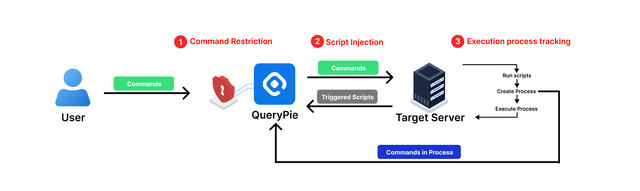
QueryPie’s 3 Unique Command Blocking Methodologies
QueryPie’s 3 Unique Command Blocking Methodologies
- Traditional Command Blocking Logic
- Script Injection Prevention
- Execution Process Tracking for Complete Blocking
These three methodologies represent QueryPie’s unique approach, which prevents command bypasses and protects servers from various security threats. For a deeper dive into the technical details of these methods, you can refer to QueryPie’s White Papers.
- Shell Native Command Control through SSH Proxy Architecture
- Blocking SSH Command Bypass Using Execution Process Tracking
QueryPie’s Differentiated Value: Innovative Approach to Blocking Command Bypass
**QueryPie has independently designed and implemented three unique command-blocking methodologies **to fundamentally prevent server command bypass execution. In particular, its technology for tracking execution processes enables the complete blocking of bypass techniques that involve combining commands within scripts or on servers.
Server command restriction technology has become a core feature of server access control solutions in line with Korea’s strict compliance requirements. As a result, Korean server access control products provide the most advanced command control technologies. When compared to global counterparts, products from Korea have undergone much deeper research and development on these technologies.
Nevertheless, the issue of command bypass remains one of the major unresolved challenges in the industry. To address this, server access control solutions in the domestic market have typically been divided into Agent-based and Agentless approaches. Agent-based products require the installation of separate agents to block command bypass, leading to additional management overhead. On the other hand, Agentless solutions do not require agent installation but often fail to block bypass attempts through scripts or the invocation of other scripts within a script.
QueryPie combines the advantages of both Agent-based and Agentless approaches by** offering superior command-blocking technology in an Agentless format**. Without the inconvenience of agent installation, QueryPie effectively tracks execution processes and perfectly blocks any attempt at command bypass. This technology provides a unique solution that is not available in the industry, and it has received strong praise from customers.
Wrapping Up
Blocking command bypass execution is a critical element of server security. If command bypass attempts are not blocked, malicious users or accidental mistakes can lead to security vulnerabilities, which could escalate into system breaches or data leaks. To effectively prevent command bypass, solutions that can consistently enforce security policies across complex system environments are essential.
Next-generation security solutions like QueryPie minimize installation burdens while tracking command execution in real-time and effectively blocking bypass attempts, enabling businesses to establish safer IT environments. These solutions help companies reduce the complexity of security management, set new security standards, and overcome the limitations of traditional security methods. Therefore, blocking command bypass execution is an essential investment in securing an organization's IT environment, ensuring long-term success and reliability.