Why QueryPie Stands Firm on Its Agentless Philosophy
November 22, 2024
Overview
The transformation of modern IT infrastructure requires an innovative shift in security paradigms. With the acceleration of cloud technologies and the adoption of container-based applications, the limitations of traditional perimeter-based security models have become more apparent. At the core of these changes lies hybrid infrastructures that combine multi-cloud environments such as AWS, Azure, and GCP with on-premises systems. Furthermore, the increase in dynamic IT assets has made it difficult to track infrastructure statuses in real time. With the rise of remote work and mobile accessibility after the COVID-19 pandemic, the need for a Zero Trust security model has become even more crucial. In this blog, we will explore new approaches and solutions for building an effective security framework in the rapidly changing IT environment.
Three Key Characteristics of Modern IT Infrastructure Changes
- Infrastructure Decentralization: More hybrid environments are emerging, combining various multi-cloud platforms such as AWS, Azure, and GCP with traditional on-premises systems.
- Dynamic IT Assets: The rise of managed Kubernetes environments like EKS, AKS, and GKE, along with the expansion of Auto Scaling and serverless architectures, has led to more flexible infrastructure, making it challenging to track infrastructure statuses.
- Increase in Remote Work and Mobile Accessibility: Remote work has become the norm post-COVID, and various business systems are being accessed on mobile platforms. As a result, security trends based on Zero Trust are accelerating.
4 Major Limitations of Agent-Based Security
Recently, the security trend is shifting more towards agentless, or agent-free, solutions. But why is this the case?
The primary advantage of agentless solutions is that they save system resources. This is particularly beneficial in various environments, as it significantly reduces the burden of management and maintenance, which is why many companies prefer this approach. QueryPie supports businesses in operating safer and more efficient infrastructures through agentless access control solutions. This allows businesses to effectively manage security threats and meet compliance requirements. The adoption of agentless security solutions is expected to continue growing, marking a key shift in the security industry.
| 1. Complex Management and Deployment |
| Agents need to be installed and maintained directly on the infrastructure. When an agent version changes or a new agent is needed, upgrading becomes an issue. Additionally, agents can sometimes clash with each other or interfere with processes. In container environments, installing and managing agents on resources with short lifecycles is especially inefficient. |
| 2. Performance Issues |
| Since an agent is essentially a program running as a process, it can consume a significant amount of CPU and memory resources. Over time, agents can cause performance issues in databases or servers, which is not a rare occurrence. |
| 3. Visibility Limitations |
| Visibility is limited to only the infrastructure resources where agents are installed. Therefore, it becomes difficult to gain full visibility over the entire infrastructure. |
| 4. Scalability Constraints |
| As mentioned earlier, in cloud and container environments, resources are dynamically created and destroyed. Installing and deploying agents based on this lifecycle can hinder the movement towards a more flexible and scalable security model. |
Strengths of Agentless-Based Architecture: QueryPie’s Choice
To provide access control and logging in environments like databases, servers, and Kubernetes without installing agents, it’s essential to understand how these environments interact with the client. The design must account for the meaning conveyed by each packet, how to provide proxy services, and various other considerations at the intersection of infrastructure and users.
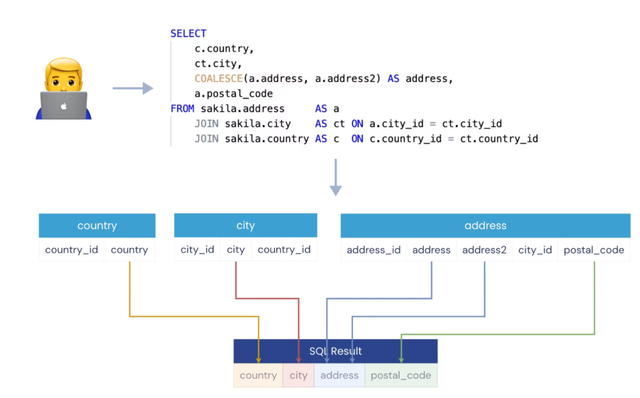
In particular, for database access control, QueryPie’s solution thoroughly analyzes SQL syntax executed by users via a parser. It ensures that users have the proper permissions to execute the SQL queries and that the third-party database client being used by the user communicates through various databases. QueryPie Proxy performs actions like authentication, encryption, query execution, and stream communication, mimicking the behavior of the database itself.
QueryPie supports over 20 different types of databases, parsing SQL syntax accurately and checking permissions to determine whether users have access to specific tables or columns. Additionally, QueryPie provides access control and logging between Business Intelligence Solutions like Tableau, Looker, and Data Warehouses.
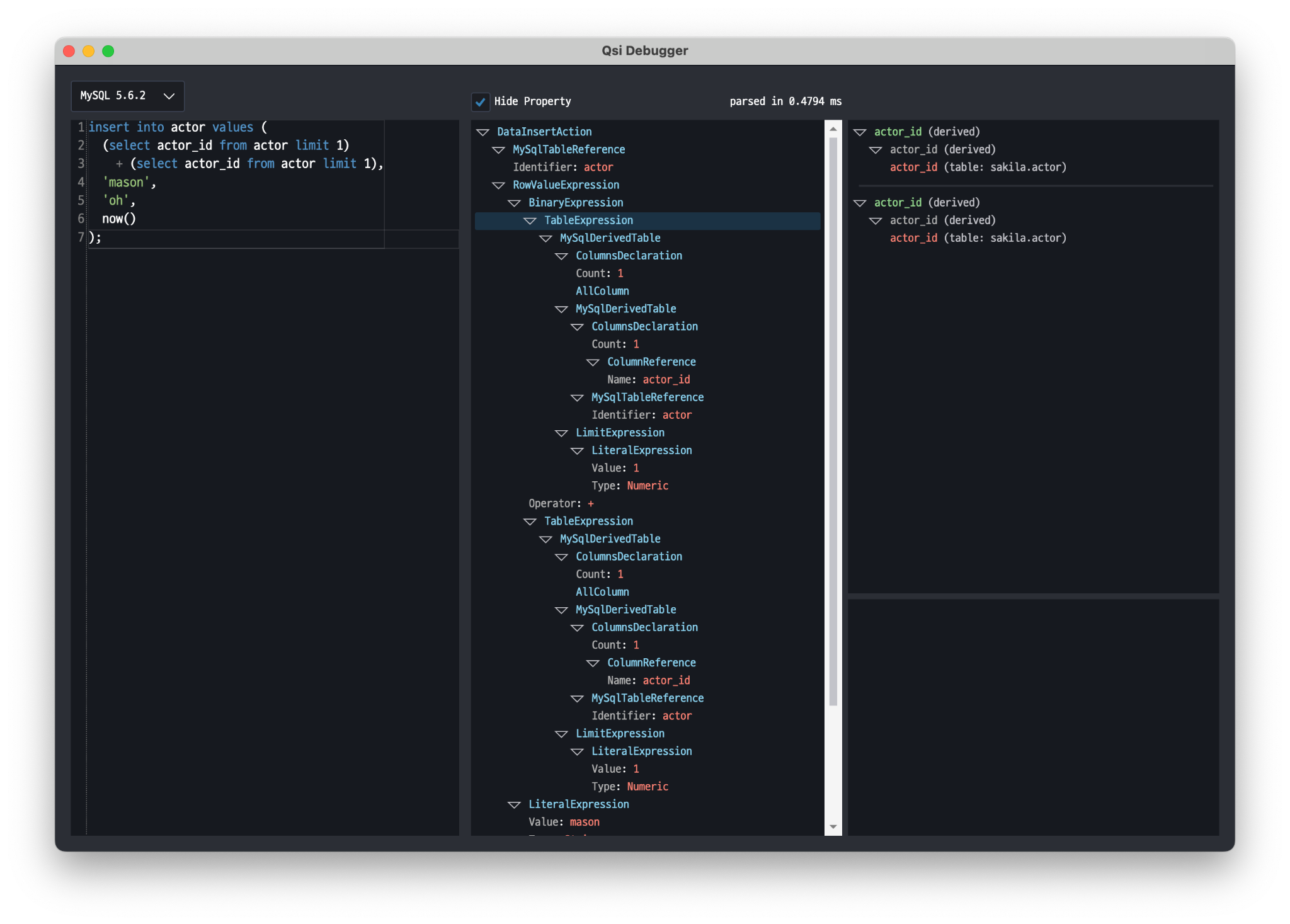
For this approach, we designed QSI (Query Structural Interface), which analyzes SSH/SFTP/Telnet/VNC, Kubernetes APIs, and all other infrastructure components, enabling Proxy functionality at every point in the infrastructure.
Ultimately, QueryPie’s core philosophy is to build security in a way that doesn’t hinder the flexibility or scalability of the infrastructure. This enables the elimination of agent deployment and maintenance while allowing each infrastructure resource to maximize its usage and provides comprehensive visibility across multi-cloud and on-premises environments.
Here’s a brief introduction to how QueryPie’s agentless technology adds value:
QueryPie DAC uses the QSI SQL parser to analyze all SQL queries executed by users, proxying packets between the user and the database. It ensures that only authorized users can access the database and execute SQL commands. Additionally, QueryPie provides table/column-level access control and can mask sensitive data.
Additionally, based on user logs, real-time query analysis and anomaly detection can be performed.
- Real-Time Query Analysis: Analyzes which SQL queries were executed and which resources in the database were accessed in real-time.
- Anomaly Detection: Detects abnormal query patterns to identify potential threats early.
QueryPie SAC performs access control and auditing on commands and file transfer activities executed by users through SSH/SFTP proxying.
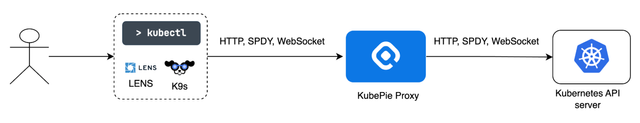
QueryPie KAC proxies all Kubernetes API calls and controls access by analyzing and managing every API call within the cluster.
Customer Case: Improvement in Data Security and Efficiency with the Adoption of Agentless Access Control
Dunamu is a South Korean startup that operates UpBit, the cryptocurrency exchange with the highest transaction volume in the world. Dunamu has dozens of AWS accounts, thousands of databases, and hundreds of database users. Initially, they used an agent-based approach for access control and logging, installing agents on all database servers and user computers. However, with constant changes in the database within the cloud environment, they found that the agent-based access control and auditing approach was no longer feasible.
After adopting QueryPie, Dunamu no longer needed to install agents. They built a higher level of data security by adding access control for actions like export/import and clipboard copying through a web-based SQL execution environment for users who needed access to the databases. This transition saved them dozens of hours annually that would otherwise have been spent installing and maintaining agents, while also providing real-time visibility into all databases.
Furthermore, QueryPie meets the infrastructure access control and logging requirements mandated by ISMS-P, the Electronic Financial Supervision Regulation, ISO 27001, and other global information security standards. As a result, QueryPie has become an essential solution for Dunamu to maintain compliance with these mandatory certifications, including South Korea's ISMS-P, the Electronic Financial Supervision Regulation, and international certifications like ISO 27001, 27701, 27017, and 27018.
Agentless Security Solution for IT Environment Innovation
In today's complex IT environments, security has become more crucial than ever. Managing hundreds to thousands of servers and databases is no easy task, and traditional agent-based approaches have shown significant limitations. In this scenario, QueryPie’s agentless security solution offers a new paradigm.
As demonstrated by the case of Dunamu, the QueryPie architecture has allowed security personnel to focus on more essential tasks, providing high-level visibility, simplified access control, and auditing capabilities. This enables the balance between security and business needs to be maintained even in the fast-paced changes of IT infrastructures.
The innovative security architecture offered by QueryPie is best experienced firsthand. Through the efficiency and innovation brought by the agentless approach, you can see how it can help solve your security challenges. Experience it now and explore how QueryPie can transform your security approach. (Link to QueryPie Virtual Tour)