Your New Ally in Data Privacy and Management: Data Discovery
In today’s society, both businesses and individuals are increasingly aware of the importance of information protection, a focus that has only grown with the tightening of legal regulations. In this environment, companies are strengthening personal data protection through various security measures, such as access control to databases, data encryption, query alerts, and logging. Particularly, when developing services that handle personal data, it is essential to identify and manage personal data located along specific paths in the database.
However, within an organization, there is always the possibility that data could enter through unexpected pathways, raising the need to broaden the scope of personal data protection. Personal data protection laws define not only information that directly identifies an individual (like a name) but also other data that, when combined with other information, can easily identify a person. As a result, businesses must establish more comprehensive personal data management strategies. This blog will delve into the importance of personal data protection and explore practical security measures that businesses can take to address these challenges.
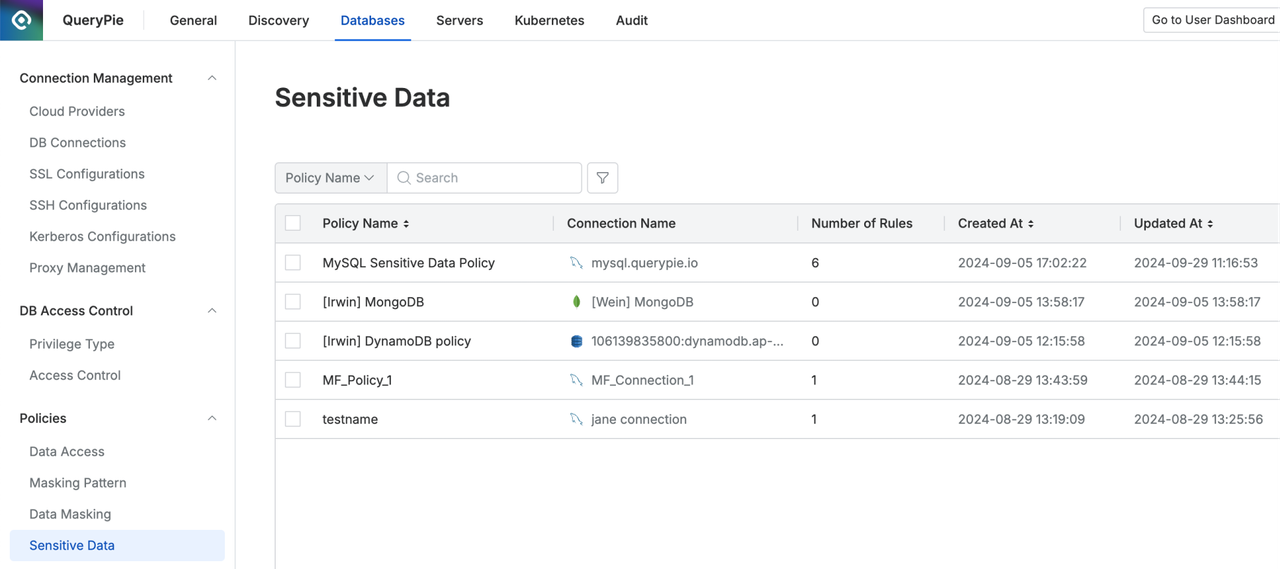
QueryPie's Personal Data Policy for Database Access Control
How Should Personal Data be Managed Within a Company?
- Identify and classify where and what types of personal data exist.
- Rather than manually accessing and reviewing data one by one, perform the discovery through automated methods, and not just once, but periodically and continuously.
- Take appropriate actions for discovered personal data (such as applying access control policies, encryption, lifecycle management, masking, monitoring queries or changes, etc.).
Data Discovery helps facilitate this series of management processes easily.
Maximizing the Efficiency of Personal Data Identification with Regular Expressions and AI
Just like a soldier with a powerful weapon can do nothing if they don't know where the enemy is, no matter how strong the security measures are, if the target cannot be identified, nothing can be done. The moment something previously unknown is revealed, you can then decide what actions to take. Knowing what types of personal data exist and what data is subject to regulations allows for appropriate responses.
The most commonly used method for identifying personal data is regular expressions (regex). The scope of extraction can vary greatly depending on how the regex is created, and in order to get the desired results, highly complex regex may be necessary. Administrators who are not familiar with regular expressions often struggle to create complex patterns and go through many trial and error processes. If tested, complex regular expressions are readily available, the administrator can save time and effort that would have been spent creating new patterns. Alternatively, if an AI model trained on various patterns is available, identification can become much simpler.
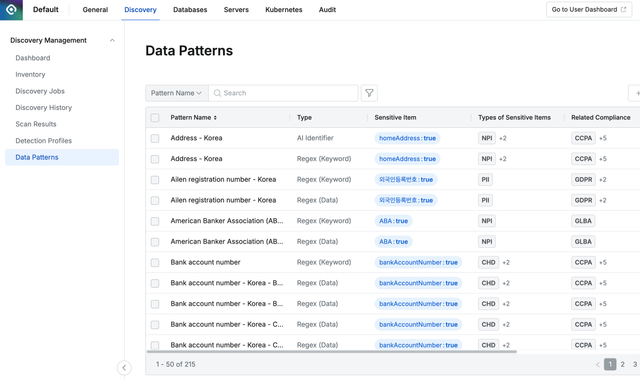
Various Patterns Provided by QueryPie
Automating Data Discovery: A Path to Cost Savings and Enhanced Security
Manually accessing and searching individual data sources to identify whether personal data exists is time-consuming and requires significant effort. According to a 2023 survey on information security conducted by the Korea Information Security Industry Association, the average number of information security personnel in companies is just 0.8. Additionally, in most organizations, the person responsible for information security often handles multiple roles rather than focusing solely on security. In such cases, unless external consulting is involved, it seems nearly impossible for an information security officer to manually search through the entire organization’s data for personal information.
Thus, by simply setting up the information security officer to periodically conduct personal data discovery through Data Discovery and scheduling regular scans, companies can significantly reduce additional costs. This approach not only improves efficiency but also strengthens security, ensuring compliance without adding extra personnel or expenses.
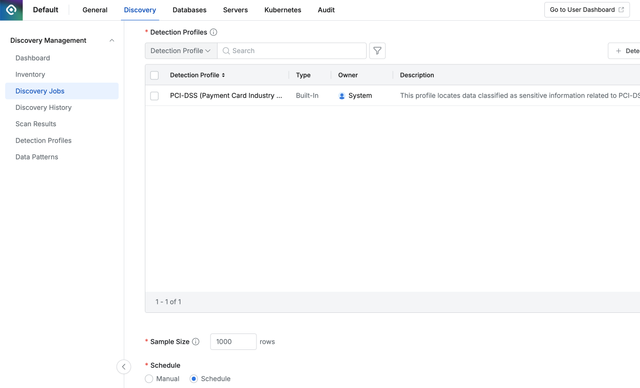
Easy and Ongoing Personal Data Discovery Through Discovery Job
AI and Regular Expressions Limitations: The Current and Future of Personal Data Identification
No matter how sophisticated a regular expression is or how well-trained an AI model is, there are still limitations in achieving 100% accurate identification. While future advancements in technology will reduce the need for human intervention, at present, identified results inevitably require human review. Only after this review can the results be finalized as the basis for policy application. Personal data tags can be used as conditions for applying policies.
In practice, QueryPie’s AIDD (AI Data Discovery) provides various features that automatically identify personal data within a company’s database and manage it effectively. By using predefined patterns and AI models, it helps reduce the effort required from administrators, while dynamically supporting the connection to access control policies by tagging the identified personal data. Additionally, continuous efforts are made to maximize discovery performance while minimizing false positives, without affecting the performance of the database. These features contribute to minimizing security gaps, helping companies comply with external regulations and internal policies, and ultimately improving overall data protection levels.
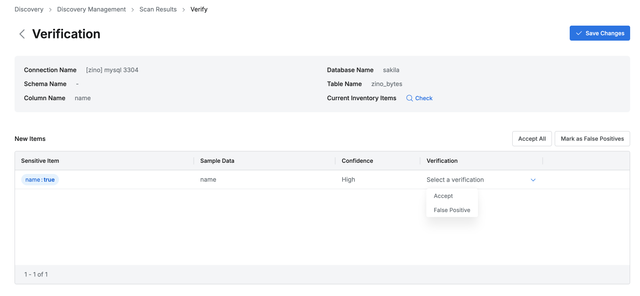
Easy and Ongoing Personal Data Discovery Through Discovery Job
In Conclusion
Through Data Discovery, companies can effectively manage security gaps that are often overlooked by simple access control policies. This allows businesses to elevate their data protection standards and develop solutions in line with information security regulations and internal policies. Data Discovery, emerging as a new ally in personal data management, will enable more companies to achieve thorough data protection.
