From Chaos to Order: Revolutionizing Multi-Cloud Kubernetes Access Control
November 22, 2024
Introduction
Kubernetes is a powerful orchestration tool for deploying and managing applications. Through my experience in developing and operating various systems like Search Service, MLOps, and API Gateway within Kubernetes clusters, I’ve found that Kubernetes facilitates the easy deployment and management of applications. It operates on a declarative structure, maintaining the desired state of resources automatically and continuously monitoring the cluster’s health. Kubernetes not only schedules applications to the appropriate nodes but also simplifies deployment, operation, and automation. Moreover, it offers a rich ecosystem for monitoring, CI/CD, authentication, and workflows, making it an ideal platform for building service environments.
However, as the scale of operations grows and environments like multi-cloud setups come into play, managing multiple clusters can become complex, requiring a deeper understanding of Kubernetes. With this increased complexity come various challenges in user access control and security management for each cluster. In this post, I will share the challenges I’ve faced while operating multiple Kubernetes clusters and propose strategies to address these issues.
Challenges in Kubernetes Operations
While Kubernetes is highly convenient and efficient for deploying and automating applications, its operation can pose significant challenges. One of the main issues is that while the dependency on Kubernetes grows, the people responsible for its management often lack a deep understanding of the platform. As a result, when problems arise, teams may struggle to troubleshoot and resolve them effectively. This gap in expertise can lead to delays in addressing issues and impact the overall stability and security of the system.
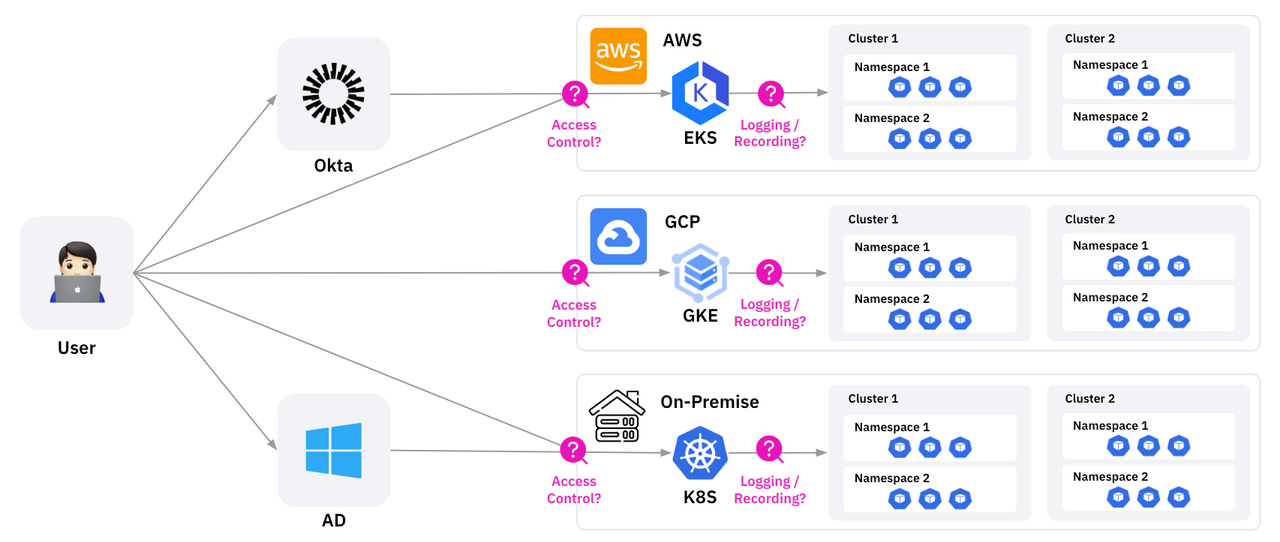
1. Lack of Kubernetes Expertise and Dedicated Teams
Kubernetes acts as an intermediary layer between applications and infrastructure, but when organizations lack a dedicated Kubernetes team or specialized staff, the responsibilities around infrastructure, applications, and security management can become unclear, leading to confusion. This results in a situation where the person responsible for Kubernetes takes on most of the operational burden. Without proper knowledge and understanding, security vulnerabilities can be exposed, and incident response can be delayed.
- Missing or Incorrect Role Configurations
- There’s a risk of accidental access to resources in other teams’ namespaces or accidental deletion of important data.
- Missed Logs and Events
- Failure to detect unusual requests or activities can lead to security incidents or delayed responses to system failures.
2. Admin Kubeconfig File Management Issues
The Kubeconfig file is crucial for authentication in Kubernetes, as it holds sensitive data like cluster credentials, API server URLs, and user certificates. Kubernetes does not store user information directly, so managing Kubeconfig files properly is key to ensuring secure access.
- Sharing Issues
- Sharing admin Kubeconfig files increases the risk of exposing authentication information to unauthorized individuals, which can result in unintended command execution, data leakage, or even loss of control over the entire cluster.
- Context Confusion
- Kubeconfig files often contain credentials for multiple clusters. If users run commands without properly verifying which cluster they are working on, they may inadvertently perform operations in the wrong environment, leading to disastrous outcomes such as accidental deletion of critical resources.
- File Storage Issues
- Storing Kubeconfig files in plain text on local disks makes them vulnerable to theft or accidental exposure.
3. Difficulty Managing Multiple Clusters
Many organizations operate in a multi-cloud environment, utilizing Kubernetes clusters across public cloud providers (EKS, AKS, GKE) and on-premise infrastructure. This creates several challenges in managing policies, certificates, and scaling resources.
- Lack of Consistency in Policy Management
- Independent RBAC (Role-Based Access Control) policies must be configured for each cluster, leading to potential inconsistencies. For example, a user may have restricted permissions in a development cluster but excessive privileges in a production cluster, creating security gaps.
- Certificate Management
- Each cluster’s certificates need to be manually monitored and renewed, which can lead to delays in certificate updates and possible outages if certificates expire.
- Complexity of Adding New Clusters
- Adding a new cluster requires updating and validating Kubeconfig files, RBAC policies, and certificates, making it a complex and time-consuming process.
4. Issues Arising from Excessive Permissions
Kubernetes offers broad access control mechanisms, but granting users broad permissions like cluster-admin can cause severe issues if not managed properly.
- Wide Access Permissions
- A user with
cluster-adminpermissions can access all sensitive resources in any namespace, including thekube-systemnamespace, where core components reside. If they accidentally delete components in thekube-systemnamespace, the entire Kubernetes cluster can be brought down.
- A user with
- Failure in Role Separation
- If the same user has excessive permissions in both development and production environments, they may confuse the two and accidentally execute dangerous commands, such as deleting production resources.
- Abuse of Permissions
- Failing to revoke permissions when an employee leaves the company or changes roles may lead to unauthorized or malicious use of their account.
5. Challenges in Audit Management and Regulatory Compliance
Audit logs are crucial for tracking user activities within the Kubernetes environment. However, default configurations do not always provide sufficient auditing, leading to security gaps.
- User Identification Issues
- Kubernetes doesn’t natively store user information, making it difficult to identify who performed an action in the event of an audit.
- Complex Policy Configuration
- Without properly configured Audit Policies, important events like secret access or failed API calls might be omitted from logs. This can prevent timely identification of security threats.
- Log Collection and Analysis Problems
- By default, audit logs are stored on the disks of each Kubernetes master node (typically three nodes), and they are not centralized. As a result, log files must be aggregated from all the master nodes for analysis, which becomes even more challenging when there are multiple clusters.
- Difficulty in Meeting Regulatory Requirements
- Regulations like GDPR and ISO 27001 require logs to be stored for extended periods and analyzed for compliance. Kubernetes' default setup doesn’t support long-term log retention or consistent policy enforcement across clusters.
Solutions to the Challenges
I have summarized the core strategies necessary to address the management and security challenges in Kubernetes operations. These solutions focus on enhancing operational efficiency and strengthening system stability through consistent application of secure authentication, access control, permission management, and audit policies in multi-cluster environments.
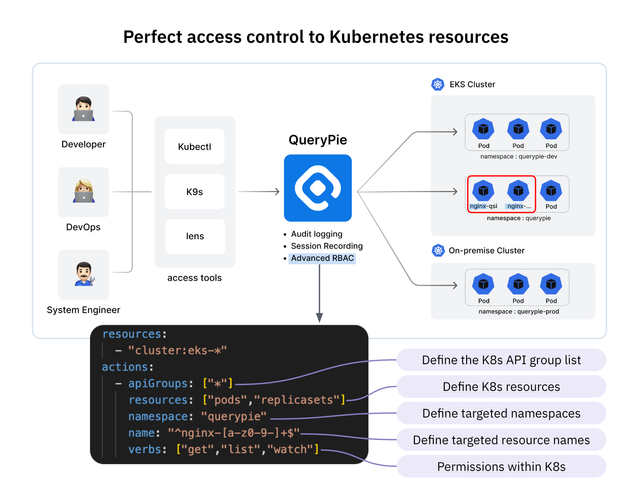
1. Enhancing Kubernetes Authentication through Integration with Enterprise User/Organization Information
By integrating with Identity Provider (IdP) systems like LDAP, AD, and Okta, user authentication and access control can be centrally managed, strengthening both security and convenience.
- Dynamic User Authentication: When users log in via IdP, temporary certificates are issued to minimize the risk of Kubeconfig file leakage.
- Organization Structure and Role Mapping: Roles are defined for user groups, and permissions for namespaces and resources are granularly configured.
- Account Management Automation: Automatically assigns permissions for new employees and revokes access for departing employees through IdP integration.
- Multi-Cluster Unified Authentication: A single authentication system provides consistent access control across all clusters.
2. Fine-Grained Access Control Based on RBAC/ABAC
Utilizing RBAC (Role-Based Access Control) and ABAC (Attribute-Based Access Control), Kubernetes access permissions need to be tightly controlled. This helps remove unnecessary permissions, improving both security and operational efficiency.
- Role Definition at the Namespace Level: Define specific roles for each namespace and restrict resource access for teams accordingly.
- For example: Developers can access only the dev namespace, and operations teams can access only the prod namespace.
- Resource-Based Access Restrictions: Limit actions (Read, Write, Delete) on specific resources such as Pods, Secrets, and ConfigMaps.
- For example: A database administrator may only have read access to Secrets, not modify or delete them.
- Pod Security Policies: Apply security requirements (e.g.,
privileged: false, image signature verification) during pod execution to enhance security, and enforce access control and monitoring for individual Pods. - Conditional Access Control: Use ABAC to control access based on user context, such as time of day or network range.
3. Multi-Cluster Integration and Management in Diverse Environments
In a multi-cluster environment, managing a mix of public cloud services (EKS, AKS, GKE) and on-premises Kubernetes clusters can increase management complexity. To address this, all clusters should be managed centrally with consistent policies and permissions applied.
- Centralized Management Dashboard: Monitor the status of all clusters (resource usage, network status, major events) in real-time to enhance operational efficiency.
- Maintaining Policy Consistency: Define RBAC and network policies centrally, ensuring they are consistently applied across all clusters to avoid configuration errors.
- Centralized Authorization Changes: Manage user permission changes centrally and synchronize them across all clusters in real-time.
- Access Logs and Audit Management: Record user actions by cluster, detecting abnormal activity patterns in real-time and enabling quick issue tracking.
4. Audit Logging and Centralized Audit Policy Management
Integrate and manage audit logs from multiple clusters centrally, applying consistent policies to trace security incidents and ensure regulatory compliance.
- Centralized Log Repository: Integrate audit logs from all clusters (e.g., Pod creation, deletion, Secret access attempts) into a centralized storage for analysis and management.
- Standardized Audit Policies: Apply the same logging and analysis policies across all clusters to improve management efficiency.
- Real-time Log Monitoring and Alerts: Real-time log analysis generates automatic alerts for abnormal access or configuration changes.
- Compliance Data Provisioning: Systematically manage necessary data to meet key regulatory requirements like GDPR, ISO 27001, etc.
5. Real-Time Verification of Kubernetes Requests
Verify resource creation, deletion, and update requests in real-time to block requests that do not comply with security or operational policies.
- Resource Validation: Ensure that the settings of requested resources (Pod, Deployment, etc.) align with security and operational policies.
- For example: Verify if a container image is pulled from a trusted registry.
- Blocking Over-Privilege Requests: Immediately block requests that a user’s permissions do not allow (e.g., attempting to delete unauthorized resources).
- Policy Automation: Automatically apply appropriate labels, annotations, and resource limits based on operational standards when resources are created.
- Pod Access Monitoring: Real-time session recording when accessing Pods through the terminal.
Benefits of Implementing QueryPie KAC (Kubernetes Access Controller)
The QueryPie team has developed a solution that practically addresses Kubernetes operational and security challenges. The key features of this solution are as follows:
- Integration with Corporate User/Organization Information
- Fine-Grained Access Control based on RBAC/ABAC
- Multi-Cluster Unified Management Across Different Environments
- Audit Logging and Centralized Audit Policy Management
- Real-Time Validation of Kubernetes Requests
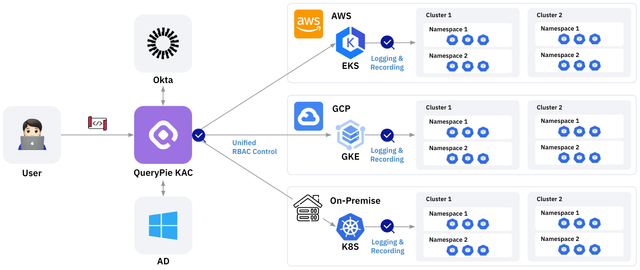
1. Enhanced Security through Least Privilege Access Control
Before Implementation:
- Manual management of user permissions often leads to over-permissioned or under-permissioned settings.
- Increased risk of security breaches due to issues like failure to delete accounts of former employees or unnecessary permission abuses.
- Sensitive data exposure potential when certain users have access to resources they do not need.
After Implementation:
With KAC, detailed access controls are set for each user at the cluster, namespace, and resource levels, enhancing security and reducing the risk of permission misuse.
2. Consistent Security Management in a Multi-Cluster Environment
Before Implementation:
- Managing security policies separately for public cloud and on-premises environments is complex and inefficient.
- Difficulty maintaining consistent security settings due to discrepancies between policies for different clusters.
- Risk of security gaps between clusters due to missed configurations during multi-cluster management.
After Implementation:
A unified security policy is applied across both public and on-premises clusters, improving management efficiency and reducing administrative burdens.
3. Automated Kubeconfig Management
Before Implementation:
- Kubeconfig files must be manually created, deployed, and updated, requiring repetition of this process across all clusters whenever user or permission changes occur.
- Issues arise due to incorrect file distribution or update omissions, potentially causing access problems or over-permissioning.
- Time-consuming tasks increase the risk of operational failures due to human error.
After Implementation:
KAC integrates with IdP to automatically generate and manage Kubeconfig files based on personnel data, maintaining consistent permission settings and minimizing the risk of errors or misuse.
4. Real-Time Monitoring and Task Transparency
Before Implementation:
- It is difficult to track who performed what actions within clusters, making it time-consuming to identify the root cause of issues when they arise.
- The inability to pre-approve high-risk operations increases the potential for security breaches.
- Lack of real-time monitoring and logging of user actions.
After Implementation:
KAC enables real-time monitoring of user activities and pre-approval of high-risk commands, providing full visibility into user actions and improving security.
5. Support for Regulatory Compliance
Before Implementation:
- Inability to effectively verify user identities or allowing access to unnecessary resources, which may lead to non-compliance with regulatory requirements.
- Kubernetes alone may not be sufficient to meet security needs, leading to inefficiencies and security gaps.
- Time and cost-intensive auditing of security systems to ensure regulatory compliance.
After Implementation:
KAC supports Kubernetes security guidelines and meets key global security regulations such as NIST, CIS, ISO 27001/27017, PCI DSS, and GDPR. It ensures continuous compliance and helps effectively address and respond to evolving regulations.
In Conclusion
As enterprise system environments diversify with public cloud, private cloud, and on-premises legacy systems, managing Kubernetes across these different environments has become increasingly complex. Each environment requires unique infrastructure and network configurations, and management practices vary by cluster, making integrated operation difficult. As a result, collaboration across teams such as development, operations, infrastructure, and security becomes more challenging, and applying consistent security and access control policies becomes more complicated.
To summarize, KAC:
- Controls and monitors Kubernetes user access, reducing unnecessary risks and enhancing operational stability.
- Enables detailed and integrated management of Kubernetes permission policies.
- Helps manage resources safely and efficiently in complex environments.
- Allows consistent policy application through centralized audit logging.
We hope this article has helped you understand the importance of Kubernetes security and access control in a multi-cloud environment.