Data Leaks: How a Small Internal Breach Can Turn into a Disaster
November 22, 2024
The Seriousness and Real Impact of Personal Data Leaks
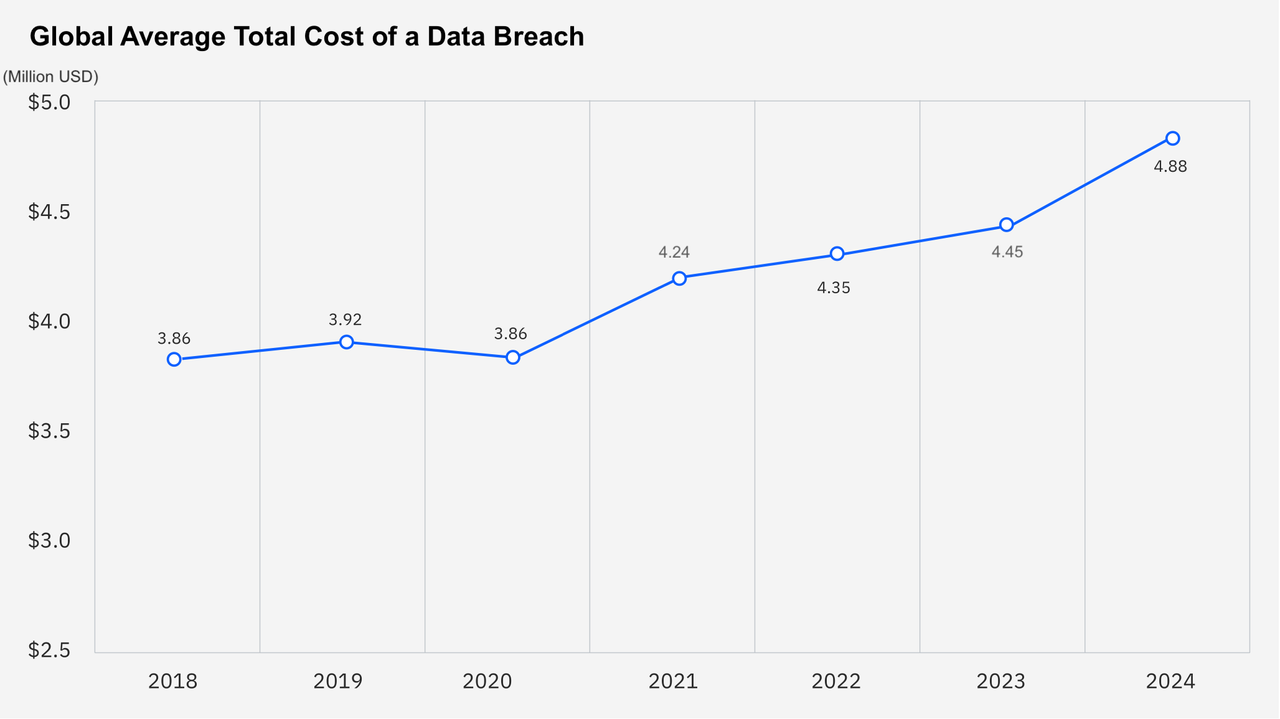
In the digital age, personal data is a critical asset, not only for individuals but also for businesses. However, when such data is leaked, it can have a significant impact on an organization’s operations and reputation. According to IBM's 2024 Data Breach Report1), the global average cost of a data breach increased by 10% from the previous year, reaching $4.88 million, marking the largest increase since the pandemic. In South Korea2), the average cost of a data breach has increased by 19% over the past three years, reaching 45.36 billion KRW, making it the second-highest in the Asia region. These breaches result in not just financial costs but also negative consequences for the organization’s reputation, customer trust, and operational stability.
The Need for Data Breach Prevention and Response
Organizations are adopting various security solutions to mitigate the risk of data breaches, but achieving complete prevention remains a challenging task. According to a 2023 report3), organizations that have implemented security AI and automation were able to detect and respond to breaches 108 days faster on average and saved $1.76 million in costs compared to those that did not. This underscores the importance of preventive measures and swift response systems. In this context, QueryPie's Database Access Control (DAC) solution helps companies proactively protect their data and respond quickly in the event of a breach.
Practical Support for Data Breach Response with QueryPie
Data breaches are one of the most severe threats organizations can face, significantly impacting a company’s reputation, customer trust, and financial stability. To prevent and respond to breaches, QueryPie’s Database Access Control (DAC) provides a strong security environment through systematic data access management and transparent activity logs. Let’s explore how QueryPie supports organizations in achieving their data protection goals by preventing breaches and analyzing the security compliance violations that occurred in breach incidents.
Case Study 1: Analysis of Data Breach Incident at Company V in Germany and GDPR Violation
Company V experienced a data breach caused by an insider attack, resulting in the leak of approximately 2 million customer records4). The leaked data included customer names, addresses, genders, dates of birth, bank account numbers, and bank codes. The perpetrator used internal knowledge to infiltrate the database. Following the incident, Company V took several actions, including changing administrator passwords and certificates, and resetting the servers. Additionally, affected customers were notified in writing, and potential phishing attacks were warned.
Analysis of GDPR Violations
The General Data Protection Regulation (GDPR)5) is a privacy law established by the EU to enhance individuals' rights to protect their personal data, ensure the free movement of personal data within the EU, and provide a unified set of data protection standards through legal obligations. GDPR clearly defines the principles for processing personal data, including legality, transparency, and purpose limitation, while emphasizing corporate responsibility.
Violation of the Integrity and Confidentiality Principle
GDPR requires appropriate technical and organizational measures to ensure the protection of personal data. However, Company V failed to prevent unauthorized access by an insider, revealing that its security measures were insufficient.
Violation of the Accountability Principle
GDPR mandates that data controllers clearly define their responsibility for data protection. Company V violated this principle by failing to establish a systematic access management and monitoring system to address internal threats.
Ensuring GDPR Compliance and Prevention through QueryPie
To address the issues highlighted in Company V's case, QueryPie offers solutions directly aligned with GDPR requirements. For systematic data access management, we grant insiders the minimum necessary permissions and block unnecessary data access. This helps prevent malicious data leaks by insiders and ensures compliance with the integrity and confidentiality principles.
Additionally, for transparent record-keeping, QueryPie provides SQL logs and data access history features, which record all data access and changes transparently. This allows for the early detection of abnormal access attempts and enables swift responses, serving as evidence that the company is fulfilling its responsibility for personal data protection. These features also contribute to reinforcing GDPR's accountability principle.
Case Study 2: User Information Leak at Company F in the U.S. and CCPA Violation Analysis
Company F6) suffered a massive data leak due to security vulnerabilities exploited by scraping, affecting approximately 533 million users. The leaked data included phone numbers, names, locations, and some email addresses, which were later exposed on hacker forums. While Company F fixed the vulnerability, they decided not to individually notify the affected users. This breach increased the risk of fraud and abuse of two-factor authentication due to the leaked phone numbers and led to criticism of Company F's inadequate response to personal data protection.
Analysis of CCPA Violations
The California Consumer Privacy Act (CCPA)7) is a law established to enhance the privacy protection of California consumers. It grants consumers the right to be informed about data collection and usage, the right to request data deletion, and the right to opt-out of the sale of their data. Additionally, businesses are required to implement security measures to protect personal data and provide timely notifications in the event of a data breach. Failure to comply may result in fines and legal sanctions.
Violation of Consumer Notification Requirement
The CCPA mandates that businesses notify consumers in the event of a data breach. However, despite the massive user data leak, Company F did not notify affected users individually. This failure violates CCPA's requirement for transparency and consumer rights protection.
Failure to Implement Adequate Protection Measures
The CCPA specifies that businesses must take reasonable steps to protect sensitive information and maintain these measures. Company F's inability to prevent scraping attacks that exploited vulnerabilities can be seen as a failure to implement and maintain reasonable protective measures.
Ensuring CCPA Compliance and Prevention with QueryPie
To address the issues revealed in Company F’s case, QueryPie offers solutions directly aligned with the requirements of CCPA. To strengthen data protection, QueryPie provides features that require notification settings and approval processes during data exports. This helps prevent unauthorized data leakage and ensures that sensitive information is protected in compliance with appropriate security measures.
Additionally, QueryPie offers sensitive data masking capabilities, which allow sensitive information to be encrypted or masked to prevent misuse in the event of a data breach. This supports a company's fulfillment of its responsibility for personal data protection. QueryPie’s activity logs and data access history features contribute to swift cause analysis and timely notification in the event of a breach.
Case Study 3: Data Breach at Company L in Japan and PIPL Violation Analysis
Company L reported a cyber intrusion that resulted in the leak of personal information of 440,000 individuals, 86,000 business partner records, and 51,000 employee records.8) The leaked information included age range, gender, and email addresses, but did not include conversation data or financial information. The breach occurred when malware infected the computer of an employee at a subcontractor in a subsidiary in Korea, and the shared authentication system was exploited. To minimize damage, Company L blocked external access, reported the incident to Japan’s Ministry of Communications, and notified the affected users and organizations.
Analysis of PIPL Violations
Japan’s Personal Information Protection Law (PIPL)9) is a regulation designed to prevent the misuse of personal data and protect individuals' rights, imposing security and management obligations on personal data handlers. It mandates notification to data subjects and reporting to supervisory authorities in the event of a data breach, with civil fines and criminal penalties for violations. The law emphasizes strengthening individuals' data sovereignty and ensuring transparency in corporate data management.
Violation of Storage Compliance Requirements
PIPL requires technical safety management measures such as access control, user authentication, and data encryption when storing data. However, the misuse of the shared authentication system indicates that Company L’s access control and user authentication systems were not sufficiently robust.
Violation of Outsourcing and Subcontractor Oversight Obligations
PIPL stipulates that when outsourcing data processing, the data handler must ensure that the subcontractor implements adequate safety management measures and that the data handler oversees the subcontractor’s compliance. Company L experienced a large-scale data breach due to security vulnerabilities in the shared authentication system with a subcontractor, highlighting a lack of adequate oversight of the subcontractor.
Ensuring PIPL Compliance and Prevention with QueryPie
By setting IP and time restrictions in database configurations, QueryPie blocks unnecessary external access, preventing the spread of malware from subcontractor computers to the entire system. This helps prevent data breaches and ensures compliance with PIPL's data storage requirements.
QueryPie's real-time monitoring and data access control features provide effective tools to oversee the implementation of outsourcing agreements. This helps verify whether subcontractors are fulfilling their security management obligations and assists in meeting the outsourcing and subcontractor oversight requirements outlined by PIPL.
Closing
Data breach incidents are one of the most severe threats organizations can face, potentially shaking a company’s reputation, customer trust, and financial stability. The cases of** **Company V, F, and L highlight the risks of insider threats, security vulnerabilities, and poor subcontractor management. To prevent and respond to these threats, a robust data protection solution is essential.
QueryPie’s Database Access Control (DAC) strengthens the security environment through data access management and activity logging. With access control, it grants insiders the minimum necessary permissions and blocks unnecessary data access, preventing data leaks. SQL logs and access history are recorded to detect and respond to abnormal attempts. Additionally, it offers features such as notification settings and approval processes during data export, sensitive data masking, and policy-based access restrictions. Through solutions directly aligned with key personal data protection regulations like GDPR, CCPA, and PIPL, QueryPie helps organizations achieve their data protection goals and maintain compliance.
QueryPie is a trusted partner for data protection and compliance, working alongside organizations to strengthen security and prepare for future threats.
References
- https://www.ibm.com/kr-ko/reports/data-breach
- https://www.aitimes.kr/news/articleView.html?idxno=29379
- https://kr.newsroom.ibm.com/announcements?item=122760
- https://www.securityweek.com/attacker-steals-data-2-million-vodafone-germany-customers/
- https://privacy.naver.com/global_support?menu=global_support_eu_gdpr_understand
- https://www.npr.org/2021/04/09/986005820/after-data-breach-exposes-530-million-facebook-says-it-will-not-notify-users
- https://privacy.naver.com/download/NAVER_CCPA_Guideline.pdf
- https://www.cpomagazine.com/cyber-security/data-breach-on-the-largest-japanese-messaging-app-line-leaks-440k-records/
- https://privacy.naver.com/download/NAVER_JP_privacyguideline.pdf