AI That Gets How You Work
QueryPie AI is here to help you achieve successful AI transformation in your life and business.
Delivering affordable enterprise AI, integrating with your existing infrastructure,
and supporting your agent-building journey—from self-service to expert partnership.
Trusted By Fastest-Growing IT Companies
Why Most AI Initiatives Fail
Everyone wants AI's transformative power, but three critical challenges stand in the way.
Low ROI
Pay-for-everyone pricing models drain budgets while most seats go unused. Companies end up paying premium ChatGPT fees for entire teams when only a fraction actively use AI tools. High subscription costs with minimal actual usage create disappointing returns, making it nearly impossible to justify continued AI investment to leadership without concrete productivity gains to show.
Management Nightmare
Getting AI to work with your current systems means tearing everything apart and rebuilding its infrastructure. IT teams have to redesign databases, reconfigure security settings, and write custom code just to make basic AI connections. Managing scattered MCP servers while protecting internal data creates chaos that most IT departments can't manage without a proper control tower.
Talent Gap
Internal teams lack the specialized knowledge to deploy AI safely at scale. Most organizations don't have dedicated AI engineers or security experts who understand both AI capabilities and enterprise requirements. This skills gap prevents companies from moving beyond basic AI experiments to production-ready solutions that drive real business value.
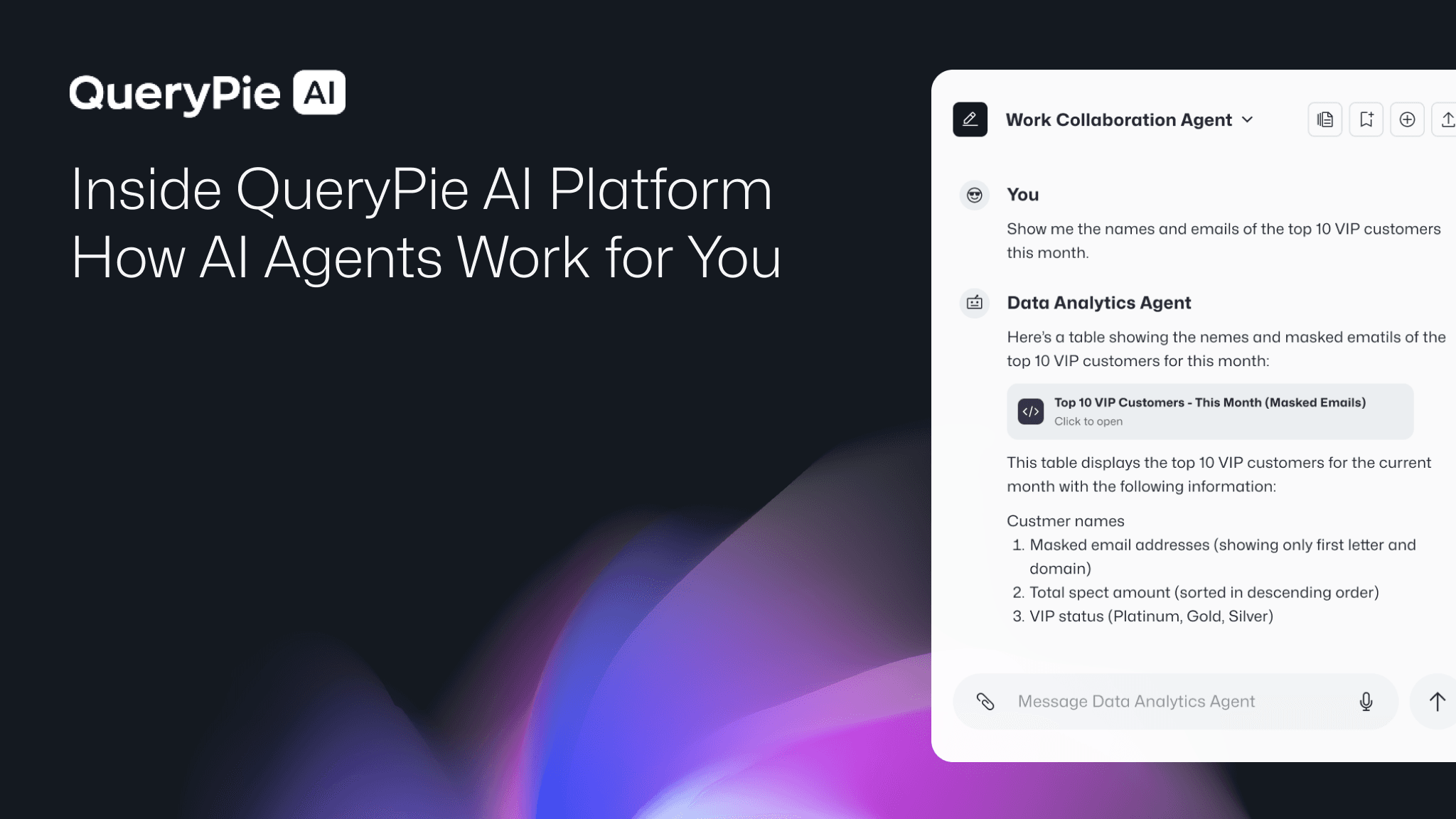
Introducing QueryPie AIP
We reimagined enterprise AI to eliminate the barriers that stop most companies—
making real AI adoption finally achievable without the pain.
Your AI Transformation Starts Here
Three ways we make enterprise AI transformation actually happen.
We are confident to make every life SMARTER, SIMPLER, and STRONGER.
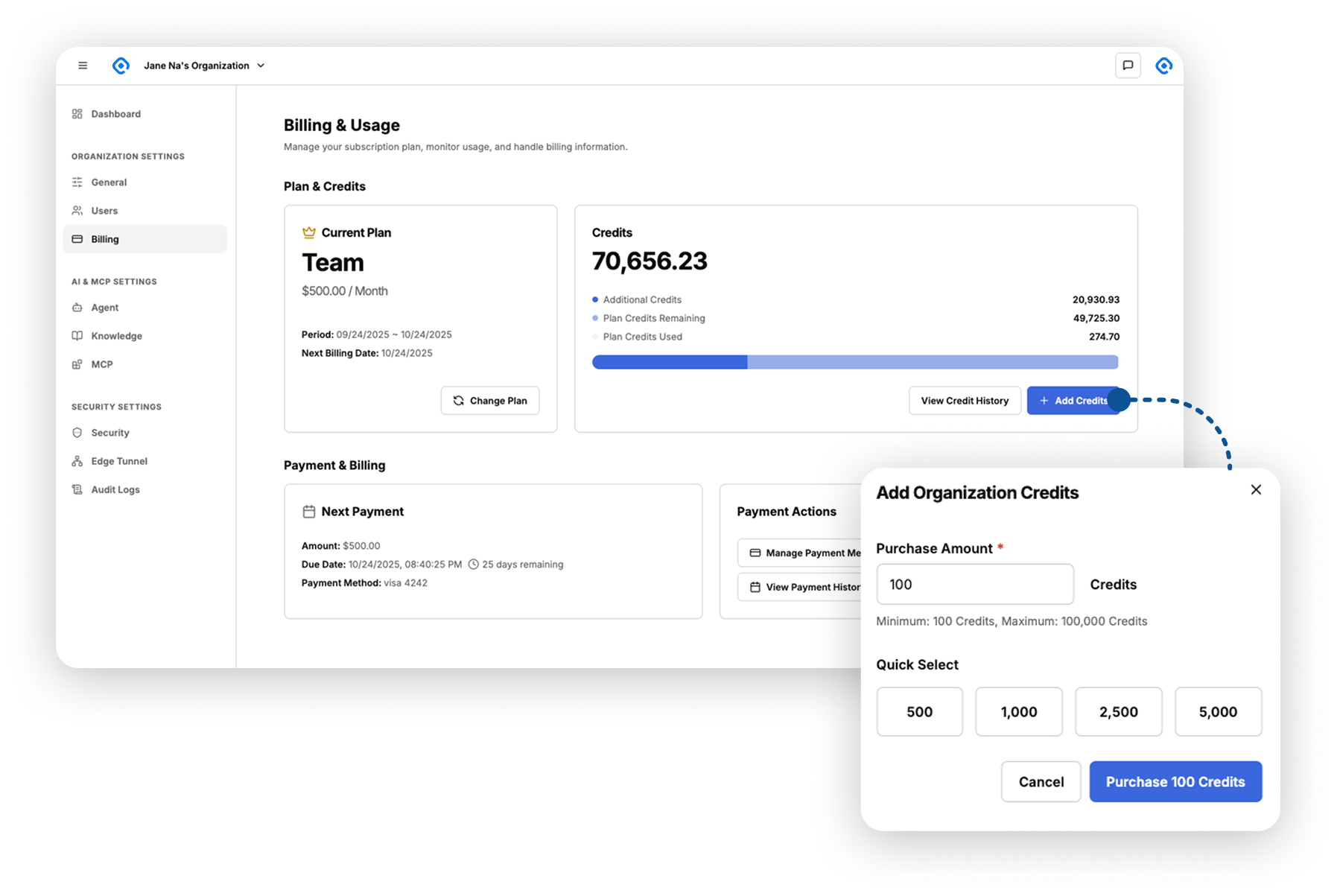
SMARTER
Usage-based enterprise AI that actually works for your business—
no waste, just results.
Replace ChatGPT with intelligent pricing
that scales with your needs and delivers real value.
Pay-Per-Use Pricing
Premium LLM Models at Your Choice
SSO & Central Management
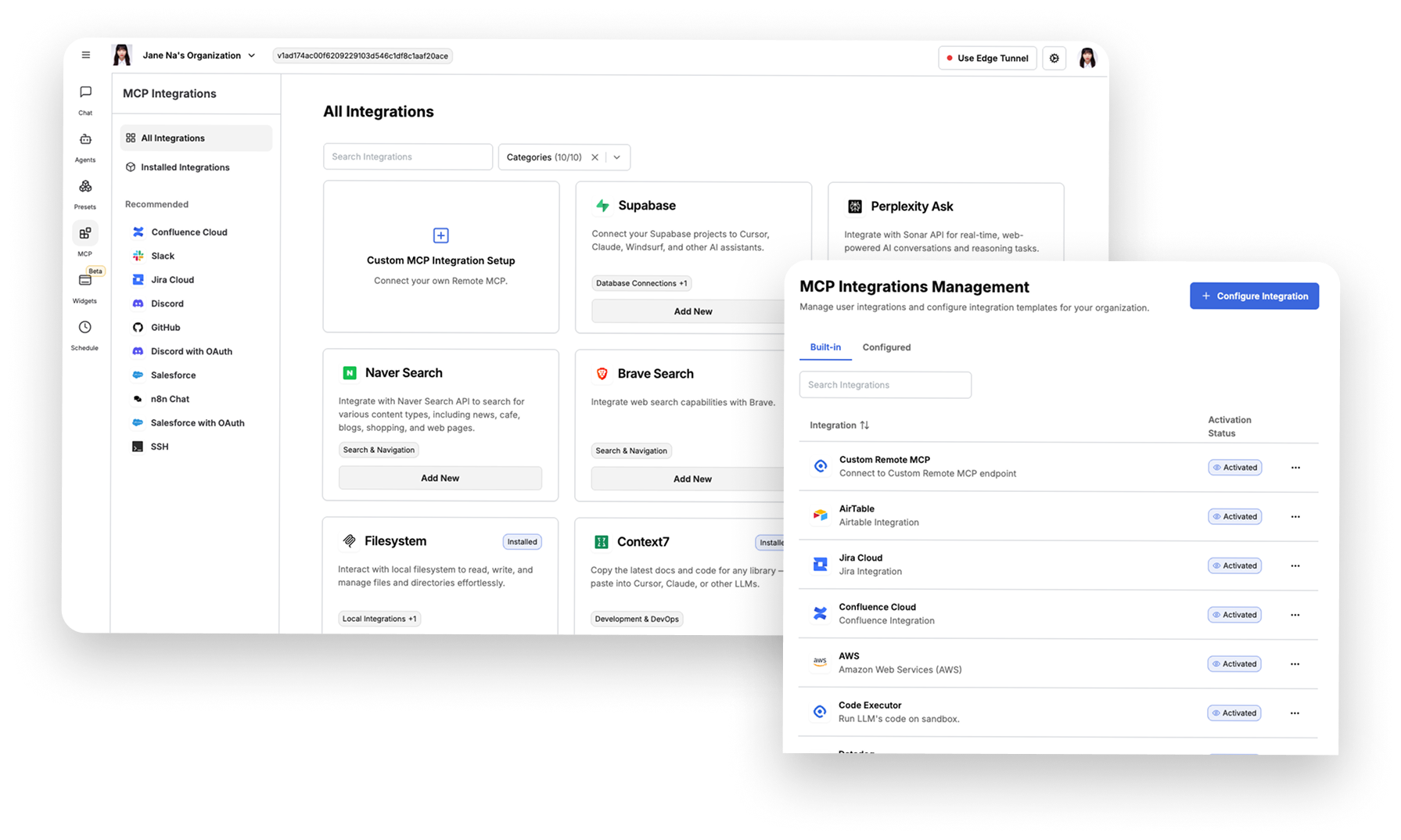
SIMPLER
One MCP Gateway platform connects all your tools—
no scattered interfaces, no integration headaches.
Transform disconnected systems into unified AI workflows
while we handle the complexity.
Smart Edge Tunneling
Easy MCP Proxy Access
Org-Level MCP Management
STRONGER
Forward Deployed Engineers (FDE) work alongside your team
to build AI solutions that deliver real business impact.
From strategy to deployment,
we ensure your AI transformation succeeds at every step.
Find Problems
Build Custom AI Agents
Make AI Work

Latest Updates & Features
Stop Thinking. Start Transforming.
Sign up in seconds and secure your 14-day free trial now.


